Solutions & Technologies
Service Provider Security
Protect users, applications, and infrastructure by extending security to all points of connection across your network.
With the acceleration of 5G, Internet of Things (IoT), and multicloud adoption, the security landscape is only growing more complex. Service providers need a modern strategy and toolset to stay ahead of the continual stream of new threats without sacrificing network performance and potentially diminishing the customer experience.

99.9% Security Effectiveness
Juniper received a “AAA” Rating in CyberRatings’ Enterprise Network Firewall Report, demonstrating a 99.9% exploit block rate with zero false positives.
How Juniper can help
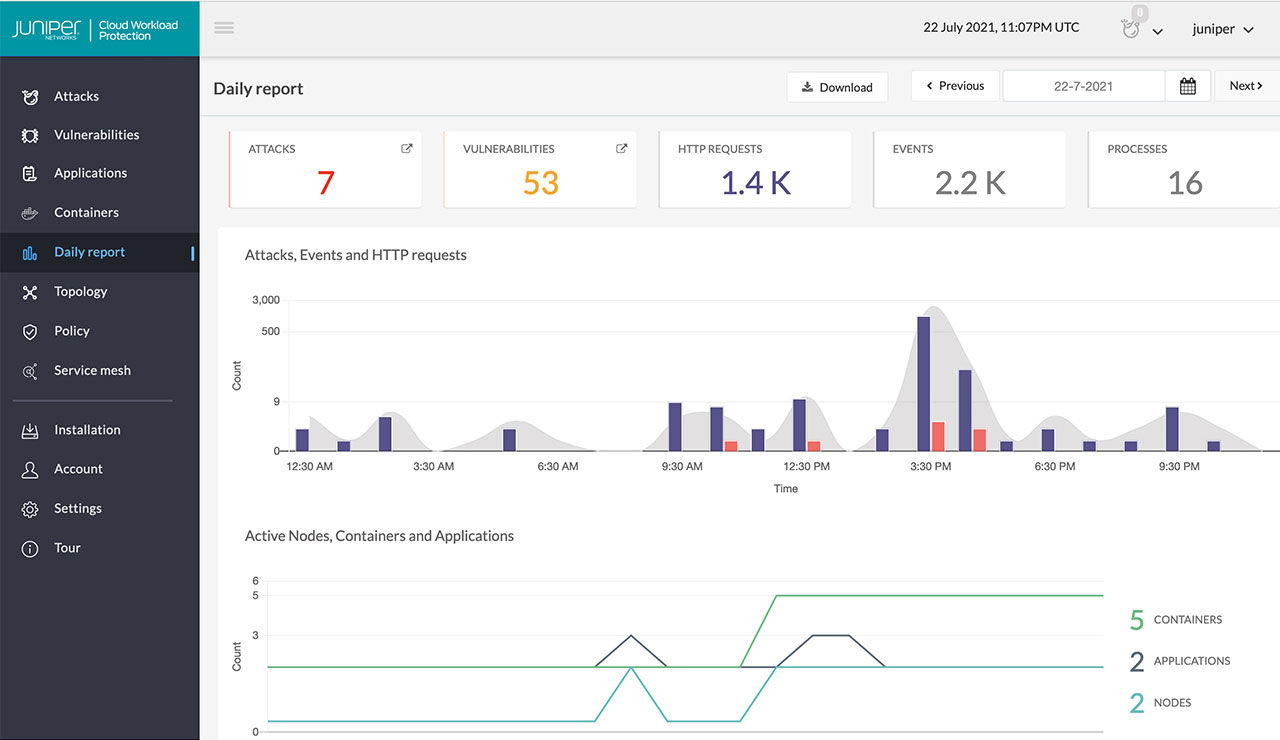
Juniper Connected Security safeguards users, applications, and infrastructure by extending threat intelligence to all connection points across your network. In addition to firewalls, we use the entire network infrastructure to detect threats on multiple fronts, so you can reliably protect against even the most advanced attacks.

5G-ready performance
You gain Carrier-Grade Network Address Translation (CGNAT) and stateful firewalling performance using the Juniper SPC3 Services Processing Card, which runs on Juniper SRX5000 Series Firewalls and MX Series Universal Routing Platforms. The solution enables you to make the 4G-to-5G transition without having to rip and replace your security infrastructure.

Inline DDoS protection
The Juniper and Corero joint distributed denial of service (DDoS) defense solution combines Juniper MX Series routers and software intelligence. It inspects traffic at the packet level while supporting infrastructure-based enforcement for real-time, automated DDoS mitigation with tens of terabits of throughput.

Integrated threat intelligence
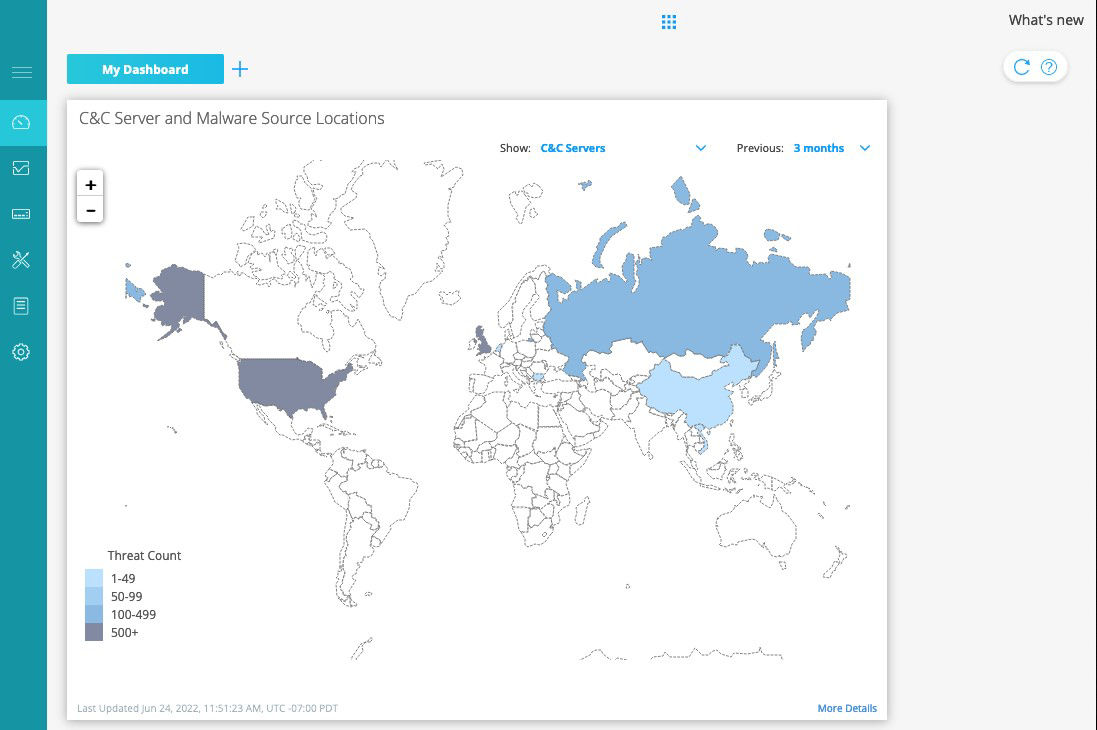
Juniper’s SecIntel real-time threat intelligence feed enables automatic, responsive traffic filtering anywhere in the network. Extended to Juniper MX Series routers, it detects, blocks, and stops command and control (C&C) traffic discovered by the Juniper Advanced Threat Prevention (ATP) solution, Juniper Threat Labs, and custom blacklists, all at wire speed.

Juniper Secure Connect
This client-based SSL VPN application allows you to securely access protected resources on your network. When combined with Juniper SRX Series Firewalls, it helps organizations quickly establish dynamic, adaptable connectivity from devices anywhere across the globe. The application extends visibility and enforcement from client to cloud over VPN connections.

Encrypted traffic insights
The latest feature of Juniper ATP Cloud and SRX Series firewalls detects malicious botnet traffic that’s “going dark” via encryption. You gain greater visibility and policy control over encrypted traffic without resource-intensive SSL decryption. There are no additional hardware or network changes to Juniper SRX firewalls required to use the feature.
Related Solutions
5G Networks
Juniper’s open ecosystem approach to 5G unlocks the full power and potential of your network. We can help you reimagine your architecture, operations, and service experience to create new business value and compete in the coming decade.
Public Cloud Security
Accelerate public cloud adoption securely with simple deployment, consistent security, and unified management experience at every level: within workloads, between applications and instances, and across environments.
Resource Center
Practical Resources
Support
Training and Community
Learn More
Videos
Blogs
White Papers
Flyers
Service Provider Security FAQs
What is Juniper Connected Security?
Juniper Connected Security safeguards users, applications, and infrastructure by extending security to every point of connection, from client to cloud, across the entire network. It helps organizations build threat-aware networks to keep attackers at bay and keep the network clear for business-critical traffic.
What use cases does Juniper Service Provider Security support?
Juniper Service Provider Security supports seven use cases:
- Mobile security gateway (SEG)
- SGi/N6 firewall
- Carrier-grade NAT (CGNAT)
- Roaming firewall
- Distributed denial-of-service (DDoS) detection and mitigation
- Data center firewall
- Intra-data center/East-West traffic protection
What is a mobile security gateway?
A security gateway (SEG) is a high-performance IPsec tunneling gateway that connects the service provider’s Evolved Packet Core (EPC) to base stations (eNodeBs and gNodeBs) on the S1/NG interface and handles connections between base stations on the X2/Xn interface.
Security gateway IPsec functionality can protect traffic as it traverses mobile backhaul by establishing an encrypted, protected connection between the service provider’s base station and EPC network. The security gateway simplifies the provisioning burden for S1-MME and S1-U (NG-C and NG-U for 5G) traffic by being a central point of IPsec concentration. (See 5G Security Strategy Considerations to learn why a security gateway is important in 5G network deployments.)
What is an SGi/N6 firewall?
An SGi/N6 firewall is a firewall connected to Evolved Packet Core (EPC)/5G Core (5GC) on a Gi LAN/N6 interface. It protects the packet core and user equipment (UE) endpoints against a variety of outside-in attacks, such as snooping and theft of information.
What is CGNAT?
Carrier Grade Network Address Translation (CGNAT) performs address translation for many purposes, including:
- Hiding topology so attackers cannot directly attack resources within the service provider’s network
- Preventing IPv4 address exhaustion by mapping a large number of private IP addresses within a service provider’s network to a small number of public IP addresses
- Connecting IPv6 endpoints within a service provider’s network to legacy IPv4 addresses on the public Internet
How does CGNAT protect your networks?
CGNAT provides address obfuscation and prevents bad actors from communicating with internal resources such as customer devices and provider host servers by hiding the source IP addresses of these devices from the outside world.
Watch High-Performance CGNAT Solution with MX-SPC3 to learn how the Juniper MX-SPC3 advanced services card transforms the CGNAT infrastructure to deliver industry-leading performance, scale, and agility.
What is a roaming firewall?
A roaming firewall is a roaming gateway connecting the Evolved Packet Core (EPC) of the home network to the EPC of the visited network to handle roaming handover.
With a roaming firewall, networks are protected through a combination of several security capabilities, including:
- Encryption of GTP-C and GTP-U traffic with IPsec
- Rate limiting of GTP-C traffic
- Prevention of GTP-C-specific attacks
- Signaling normalization and modification of GTP-C traffic, including 3GPP release interoperability
What is DDoS detection and mitigation?
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
Juniper’s DDoS detection and mitigation is an industry-leading volumetric DDoS firewall that provides real-time DDoS filtering capability at the industry’s fastest rate to prevent DDoS attacks within 5–10 seconds. (See Juniper and Corero Joint DDoS Protection Solution to learn more.)
What is Juniper Zero Trust Data Center Security?
Juniper Zero Trust Data Center Security protects hybrid data centers by operationalizing security and extending zero trust across networks to prevent threats with proven efficacy. It checks all incoming and outgoing traffic, so customers can validate and grant access to the rightful users and devices to the data center.
What are the features and benefits of Juniper Zero Trust Data Center Security?
Juniper Zero Trust Data Center Security solution helps with the following:
- Centralized visibility and analytics for all applications and data, including encrypted data and infrastructure
- Consistent policies across firewalls (all form factors, from managing via a single UI to reducing operational complexity to allowing scalability)
- Shared automation and intelligence at every point of connection across the entire infrastructure, making automated threat response a click away
- Macro- and microsegmentation to control who and what can access the network resources and reduce the attack surface while preventing lateral threat propagation
- Advanced threat services that use the power of AI/ML to detect sophisticated threats and block them
(See the Juniper Zero Trust Data Center product portfolio to learn more.)
What is Juniper Intra-DC/East-West Traffic Protection?
Juniper Intra-DC/East-West Traffic Protection is security enforcement that prevents attackers from moving laterally inside on-premises or cloud data centers by creating microsegments that limit the impact of a successful attack.
Where can I get more technical information?
For security technical content and resources for service providers, visit the TechLibrary Connected Security page.
Gartner Magic Quadrant for Network Firewalls, by Rajpreet Kaur, Adam Hils, Thomas Lintemuth, 19, December, 2022.
Gartner Critical Capabilities for Network Firewalls, by Rajpreet Kaur, Adam Hils, 17 January 2022.
Gartner and Magic Quadrant are registered trademarks of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner®, Magic Quadrant and Peer Insights™ are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.