What is an Adapative Security Policy?
What is an Adaptive Security Policy?
An adaptive security policy allows administrators to quickly adapt to the ever-changing security landscape to ensure they can protect their networks with minimal time and effort.
Traditionally, the typical network security policy is very static and its policy rule structure is as follows:
|
Rule Number |
Source Traffic Match Criteria |
Destination Traffic Match Criteria |
Firewall Action |
Logging Action |
IPS |
|
1000 |
Any |
MyCriticalServers |
Permit |
Log |
Disable |
The logic for each rule is that for a particular traffic match criteria, network administrators can configure one set of security actions.
However, security operating environments are rarely static in nature. Network policies that you want to enforce under normal conditions could be quite different from the network policies that you want to enforce when the network is under a significant attack, or when your network is already compromised and the security team is attempting to identify and isolate the compromised assets.
Static Network Security Policy Challenges
A static policy model poses significant operational challenges of adapting to security challenges. For example, when a security team realizes their network is under attack:
- They must first process thousands of rules in the rule table, one at a time to determine how to adapt those rules.
- Make changes to a multitude of rules and push them out to the firewall policies. As a result, precious security administrator’s cycles are spent on rule modifications instead of focusing on isolating and remediating the network from attacks.
- Avoid the risk of breaking some of the mission critical services. The likelihood of this is quite high at this stage because of the high volume of unplanned changes.
- Once the threat is isolated or mitigated, revert all rules back to the normal profile. The chances of mistakes, service outages, and so on, exist here as well.
It is crucial that the cyber security teams conduct normal, as well as, attack preparedness scenarios for an improved security strategy.
What are Dynamic Policy Actions?
Junos Space Security Director introduces an innovative capability called Dynamic Policy Actions to simplify the workflow of creating different security actions, in advance, that the team can take under different environmental conditions. Security Director leverages a user intent policy framework that allows policies to dynamically adapt to changing conditions in a volatile threat landscape.
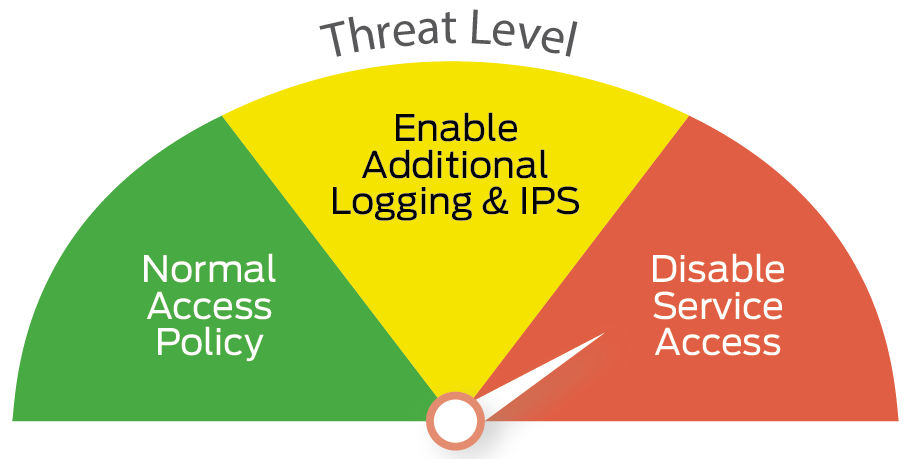
The dynamic policy actions workflow contains the following steps:
- Creates different custom environment variables that influence different rules.
- Uses the conditional evaluators based on these variables in the network security policies.
- Tests different profiles, ahead of time, to ensure that the rule behavior functions as planned.
- When a change in the environment condition is identified, changes the value of the variable to reflect the current risk situation.
- Auto-calculates the changes to the relevant rules, and based on the network administrator’s approval, pushes out these changes to the entire network as required.
With dynamic policy actions in place, the rule table adds a new environment condition column and now looks like:
|
Rule Number |
Source Traffic Match Criteria |
Destination Traffic Match Criteria |
Environment Condition |
Firewall Action(s) |
Other Actions |
|
1000 |
Any |
MyCriticalServers |
ThreatLevel=Green |
Permit |
Log |
Benefits of Dynamic Policy Actions
✓ Simplifies creation of security actions
✓ Reduces threat reaction time
✓ Reduces the probablity of manual errors
✓ Helps reduce business risks by streamlining security operations
In advance, administrators can create different security actions for the security team use as they test the system’s behavior under different environmental conditions.
Threat reaction time is reduced allowing administrators to quickly remediate security threats. During critical situations, administrators must focus on identifying the attacks and, with environment variables configured, they can quickly manipulate the rules table.
The probability of manual errors is reduced, especially during critical events when a large number of firewall policy rules need to be edited. Additionally, by streamlining security operations, business risks are reduced for normal and dynamic conditions.